Keeping one step ahead of potential threats is critical in the ever-changing cybersecurity arena. Threat modeling is a systematic method for cybersecurity professionals to identify, prioritize, and mitigate possible threats to a system or organization. In this blog article, we will delve into the world of threat modeling and its delicate relationship to threat intelligence, offering junior cyber security researchers valuable insights on improving their defense systems.
Understanding Threat Modelling
Threat modeling is a proactive method that identifies, classifies, and prioritizes potential system threats. It enables cybersecurity specialists to assess a system’s security status and apply appropriate remedies.
In the first stage, define the system’s scope and learn about its architecture, components, and data flows. Identify the assets and resources that require protection, such as sensitive data, servers, programs, or user accounts. Enumerate potential threats and vulnerabilities, considering both internal and external variables that could affect the system.
After identifying threats, evaluate their significance and likelihood. Prioritize risks according to severity and likely consequences. Finally, devise ways to mitigate the identified risks, put in place security measures, and regularly monitor the system for emerging threats.
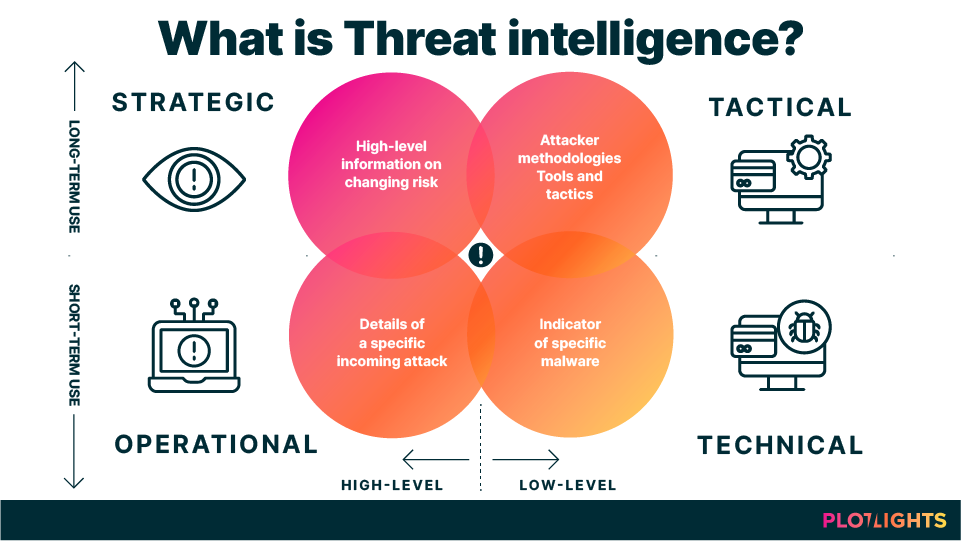
Connection with Threat Intelligence:
Threat intelligence is critical for improving the effectiveness of threat modeling. It entails obtaining and analyzing data about prospective threats, including their tactics, methods, and procedures (TTPs).
Incorporate threat intelligence feeds to help detect threats, as they provide real-time data on cyber threats. Stay current on the newest attack vectors and vulnerabilities affecting your system. Improve risk assessment by using threat intelligence to determine the likelihood and impact of individual threats. Use threat indicators and context from threat intelligence to refine risk assessments continuously.
With threat intelligence, mitigation techniques can be more effectively tailored. Create plans based on threat intelligence to counter particular risks, and be flexible enough to adjust plans as the threat environment changes. Incident response is enhanced when threat intelligence is incorporated into incident response strategies. Use threat intelligence indicators of compromise (IoCs) to identify and address security events quickly.
To sum up:
For novice cyber security researchers, threat modeling becomes an even more potent tool when paired with threat intelligence. Researchers can create robust defenses by comprehending the workings of their systems, seeing possible attacks, and utilizing timely threat intelligence. In a time when cyber threats are constantly changing, protecting digital assets and upholding a robust cyber security posture need a proactive and knowledgeable approach.