Today, we’ll look at threat hunting, a dynamic and proactive approach to cybersecurity that allows experts to discover and neutralize any dangers lurking within their networks actively. This post will explore the intricacies of threat hunting, providing practical insights and strategies to help you identify and mitigate cyber threats.
Understanding Threat Hunting:
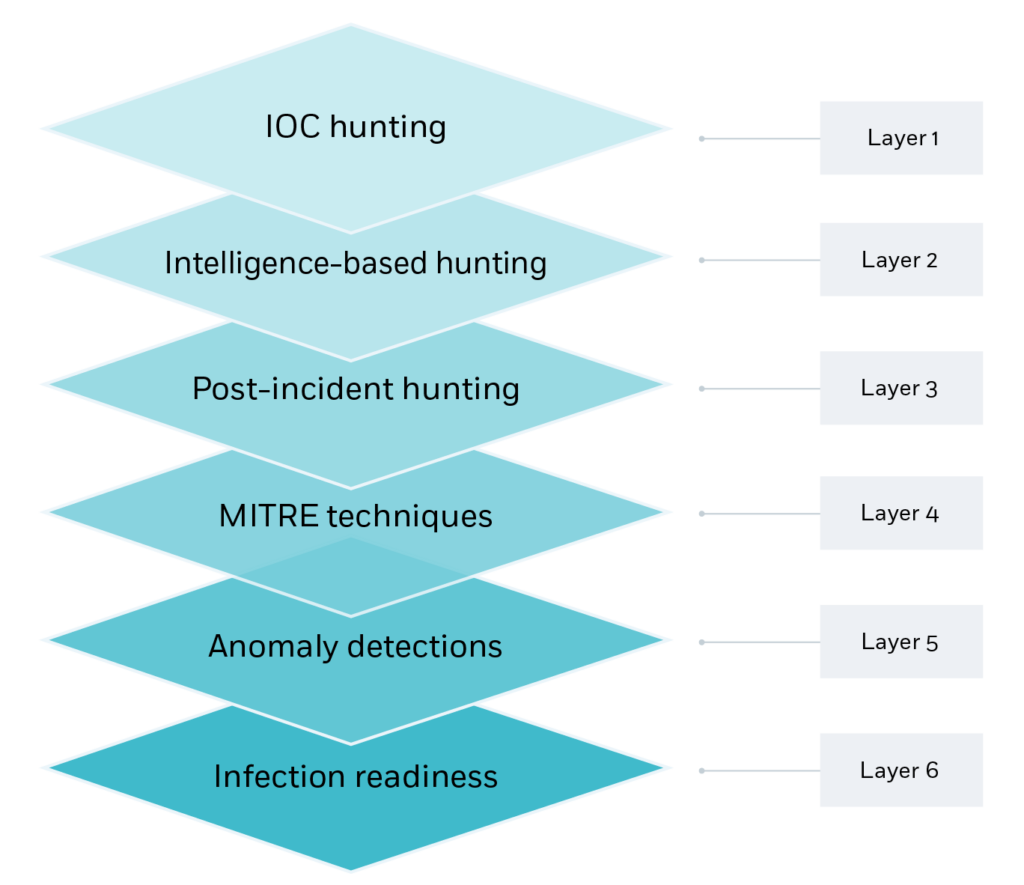
Threat hunting looks for indications of compromise (IoCs), anomalies, and unusual activity that could circumvent typical security procedures. It’s similar to being a detective in the digital realm, continuously looking for indicators of criminal activity.
Threat Hunting Process:
Preparation: Effective threat hunting begins with adequate planning. Understand your network architecture, identify essential assets, and set specific objectives for your hunting trips.
Data Acquisition and Analysis: Collecting and analyzing information are critical components of threat hunting. Logs from many sources, including network devices, endpoints, and security systems, are crucial. Tools like Splunk and Elasticsearch can assist in aggregating and analyzing massive amounts of data.
Hypothesis Generation: Develop assumptions regarding potential dangers or suspicious actions based on collected facts. These hypotheses serve as a foundation for further inquiry.
Investigation and Triage: Conduct specific investigations to support or reject hypotheses. This could include reviewing network traffic, analyzing log files, and performing forensic analysis on suspect endpoints.
*Response and remediation: In the case of a confirmed threat, work with incident response teams to launch prompt and efficient responses. This could include isolating hacked systems, preventing malicious traffic, and applying patches or updates to susceptible assets.
Tools and Techniques:
While the human aspect is critical to threat hunting, using the correct tools and procedures can significantly improve performance.
- The SIEM Platforms: Platforms such as LogRhythm and QRadar offer centralized log management and extensive analytics features.
- Endpoint Detection and Response (EDR) Systems: Solutions like CrowdStrike Falcon and Carbon Black provide real-time visibility into endpoint activity.
- Threat Intelligence Feeds: Subscribing to feeds from credible sources can provide helpful background for recognizing emerging risks and indicators of compromise.
Conclusion:
To summarize, threat hunting is a proactive strategy for cybersecurity that allows professionals to keep one step ahead of cyber adversaries. Adopting a digital detective attitude and utilizing the appropriate tools and tactics may strengthen your organization’s resilience to emerging cyber threats.
Stay tuned for future postings where we’ll go over advanced threat-hunting tactics, real-world case studies, and hands-on exercises to help you improve your skills even further.
Also please check the open-source threat intelligence tools with links:
MISP: Malware Information Sharing Platform & Threat Sharing
MISP is a comprehensive platform for sharing, storing, and correlating structured threat information.
OpenCTI: OpenCTI
OpenCTI is an open-source platform for managing cyber threat intelligence knowledge and observables.
Stix-Shifter: Stix-Shifter
Stix-Shifter is a library facilitating integration with the STIX (Structured Threat Information eXpression) standard.
YARA: YARA
YARA is a tool for identifying and classifying malware samples based on rules created by security researchers.
Yeti: Yeti
Yeti is an open-source threat intelligence platform for aggregating, enriching, and correlating threat data.
IntelMQ: IntelMQ
IntelMQ is a solution for managing and automating the processing of cybersecurity threat intelligence.
ThreatIngestor: ThreatIngestor
ThreatIngestor is an event-driven collection tool for pulling threat intelligence data from various sources.
Mitre ATT&CK Framework: Mitre ATT&CK Framework
The Mitre ATT&CK Framework is a knowledge base describing actions and behaviors of cyber adversaries.
AIS is an open-source threat intelligence sharing platform.
Vulners Database: Vulners
Vulners is a comprehensive vulnerability database providing information about software vulnerabilities, exploits, and patches.
cif: Collective Intelligence Framework
cif is an open-source intelligence sharing platform aggregating indicators of compromise.
Mitre CALDERA: Mitre CALDERA
Mitre CALDERA is an automated adversary emulation system for creating and executing adversary simulations.
Last note for you: please check Mandiant’s Threat Intelligence Reports and SocRadar’s free tools
Feel free to explore these tools to enhance your understanding of threat intelligence and cybersecurity. Always use them responsibly and in compliance with relevant laws and regulations.
Happy hunting!